Xyber vs Oblivion
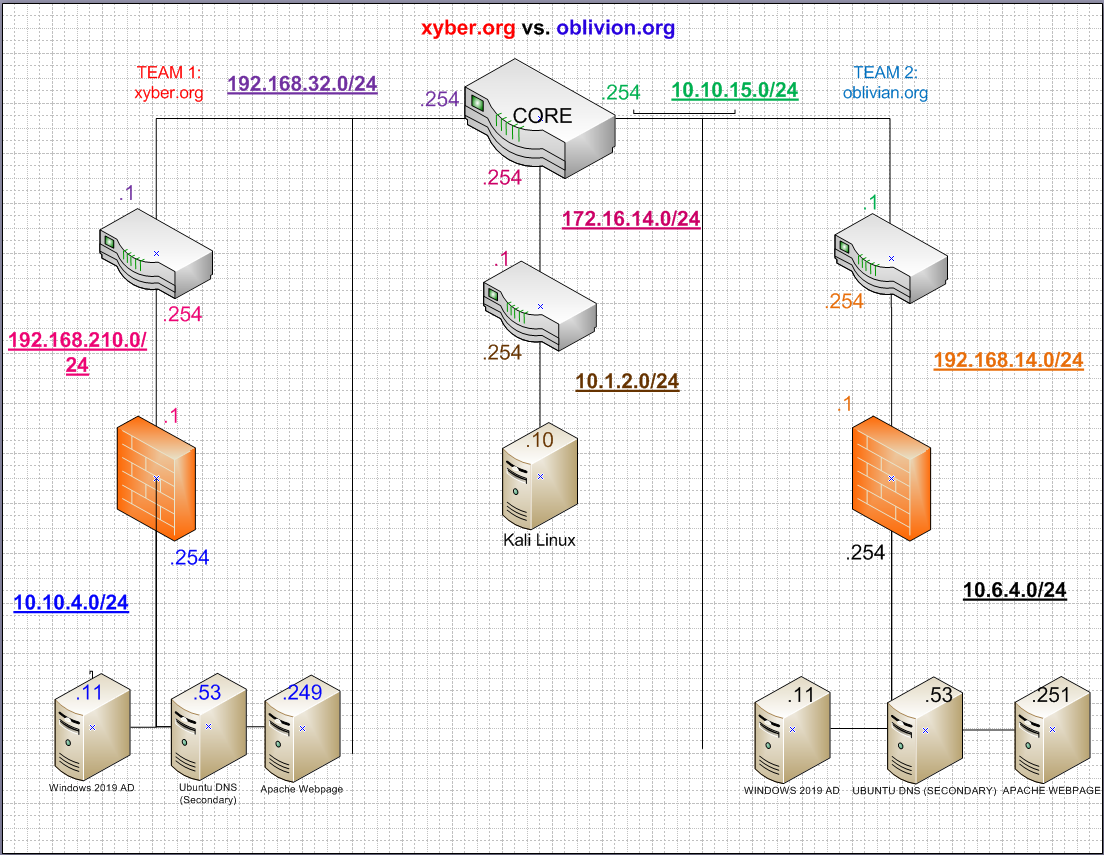
Here's Xyber and Oblivion. These networks route through a central core router and someone in Kali is listening just two hops away...
Sitting in between them is a Kali Linux box — aware of the routing paths, enabling it to perform man-in-the-middle attacks. The goal was to simulate real-world inter-network communication, while demonstrating how attackers can intercept and manipulate traffic between corporate environments. This lab taught me the importance of visibility, segmentation, and detection.