5/18/25 - Cybermart: The Hackable Retail Experience
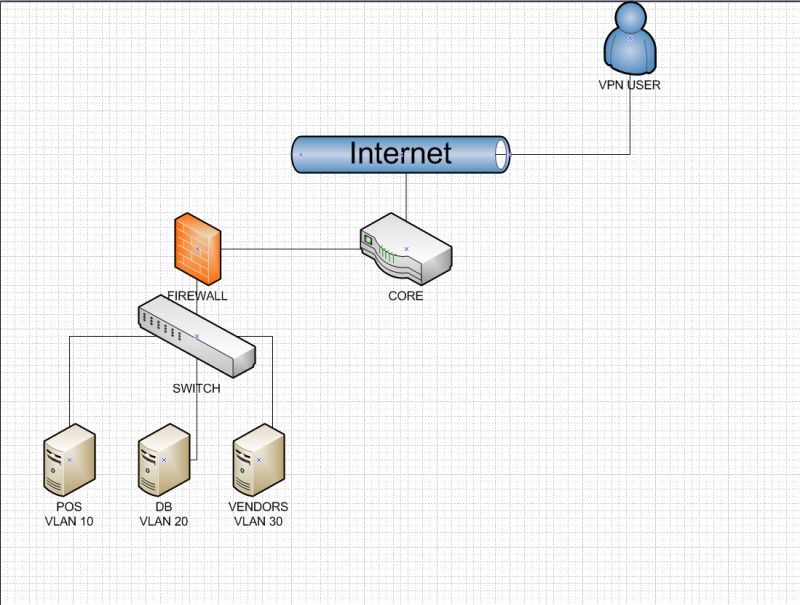
Cybermart was a really fun project — a full POS (Point of Sale) retail environment designed to be hacked. Just like Cloudrunner brought city infrastructure to life, Cybermart brings commerce to the battlefield. We're simulating everything from front-end registers, customer checkouts, inventory systems, and even a transactions tracking. POS systems (VLAN 10) running on Windows 7 paired with XAMPP. Each terminal has a local database that stores data; such as transactions, inventory, time, and dates. Then there's a master DB on a different network with cronjobs running PHP scripts that inject transactions (fake_transactions.php) and a Python sync tool (pos_sync) that pushes all data from all POS systems to a central DB sitting on VLAN 20. Firewall rules allow communication with VLAN 10 and VLAN 20 and to top it all off Cybermart has a 'Vendor' network 'FizzCore' that has VPNs credentials to the network however there lies a misconfiguration that FizzCore can talk to POS systems...
Cybermart took about a month to design and build — a true passion project born from countless hours of diagramming, revising, and rethinking how each piece fits into a real-world retail infrastructure. I hit that creative flow state more than once — you know, when ideas just click and then suddenly "what if we add this..." kicks in. The final network diagram is deceptively simple but carries layers of depth and intention. At its core, Cybermart runs on an Aruba 2540 Layer 3 switch acting as the backbone router, connecting to a pfSense firewall that governs the entire internal network. A basic HP Layer 2 switch feeds trunked VLANs into an ESXi hypervisor, hosting all the virtual machines. ESXi made VLAN tagging seamless, and pfSense made segmentation and access control straightforward — especially with its OpenVPN wizard. Once connected via VPN, users land in the Vendor VLAN — where a misconfiguration allows access to register systems but not the database VLAN, creating a perfect entry point for red teamers. From there, attackers must explore lateral movement strategies to reach localized register databases or even the centralized master database — the heart of Cybermart’s fake transaction flow. This project sharpened my network engineering and offensive thinking skills in one go. It’s a scenario that blends realism with intentional flaws, making it one of my all-time favorite builds.!